Access Control Matrix (ACM)
Hello Technophiles! Welcoming back to another article. This article deals with the Android OS architecture and its layers. Before getting to know what is access control matrix, let’s answer what is access control?
Access control describes who can do what to whom. In order to mathematically represent this, we are using something called Access Control Matrix (ACM)
Thus, ACM is nothing but a matrix that describes the rights of subjects over objects.
Subjects -> Refers to users
Objects -> Refers to files or directories
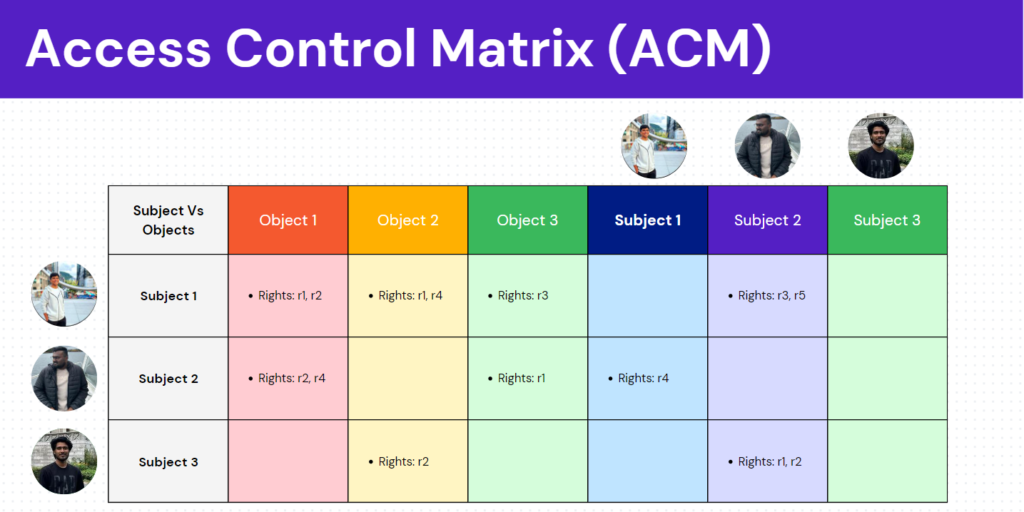
Object set always encloses subject set (i.e every subject is also an object)
Now the question arises that why the object set always encloses the subject set? In terms of OS, subjects can access and communicate with other objects. That is the reason we have the subjects on the object’s column as well.
Subject = {s1, s2, s3, …}
Object = {o1, o2, o3, …}
Rights = {r1, r2, r3, …}
Interpretation – A {Sij, Oij} = {r1, r2, ….., rn}
Now let’s look at the primitive operations that are done in Access Control Matrix (ACM)
- Create a subject
S’ = S U {s}, O = O U {s} where s belongs to S
- Create an object
S’ = S, O = O U {o} where o belongs to O
- Destroy a subject
S’ = S – {s}, O = O – {s}, where s belongs to S
- Destroy an object
S’ = S, O = O- {o} where o belongs O
- Enter a right
a[s,o] = a[s,o] U {r}, where s belongs to S and o belongs to O
- Delete a right
a[s,o] = a[s,o] – {r}, where s belongs to S and o belongs to O
The transition in the matrix is cause by commands which are sequence of primitive operations. When transition occurs, the protection state of a system will change. Such a change is modelled as ACM state transition.
The rights (example: r1, r2,…) denote the access that is provided to each individual. In addition to that, there are special rights that are used based on the role specified to that subject. One of the notable special rights is Right: Own. The special right own give rights to change all entries in a column where an owner of an object can modify and change the access.
Similarly, there are other special rights that are granted based on the access that is required.
In simple terms, this is what access control matrix is and its definition. I hope you got the basic understanding of access control matrix and its operation
Make sure you rate or comment this article and if you are finding it more useful do share & subscribe because that encourages me to write more
Cheers! Until next time…❤️
